Secure to the Core
The Protection of Your Data is Our Primary Commitment
Secure to
the Core
The Protection
of Your Data is
Our Primary
Commitment
Contact us via the links below or call 0161 883 1685 to speak to a member of our team
The Art of Cyber Security
The Cyber Security Mindset
Many senior leaders live under the misapprehension that Cyber Security is a Science, you simply give IT a budget and they buy applications to protect your business. Sadly, that’s only part of the story, users press buttons everyday and the envelope of what needs protecting grows.
No business is 100% cyber secure, even those operating without computers still use banking apps and billing software on their mobile devices. All businesses and all individuals are subject to cyber threats.
Warning: Don’t believe any supplier who says they can make you safe, no single provider has a full suite of applications and tools to make you Cyber Safe.

Its important that senior management in any business understand the balance of risk v flexibility they have in their business. A business without some form of Risk Register to track cyber concerns is likely to have problems.
A good IT partner will offer to work with the internal team on a regular review basis to monitor – identify – mitigate – move on with risk management.
The cyber safety of your business is only as good as the weakest link, some examples we have seen regularly may help your understanding:
Weakest Link Examples
Greenlight Knowledge Base Validation
With 100’s of years of experience (Corporate/SME/Public) in the team we have created a dynamic Cyber Security Master Checklist and identified mitigation options to protect our clients and colleagues.
Every week several Greenlight Computers clients are audited by their clients, audited by 3rd parties or asked to comply to the latest insurance rules, as the insurers try to avoid risk. We have also collected knowledge of supplier cyber solutions, IT industry recommendations and ethical hacker knowledgebases to learn.
Greenlight Computers have taken all those requirements and consolidated them into our Master Checklist.
In 2021, during covid we commissioned the Greater Manchester Cyber Foundry team of 4 leading Universities (The University of Manchester, Manchester Metropolitan University, Lancaster University, University of Salford) to review and critique our Master Checklist through an ERDF research grant. That project completed in January 2022 refining our Master Checklist and providing an excellent baseline against which we can assess the many different client scenarios we work with.
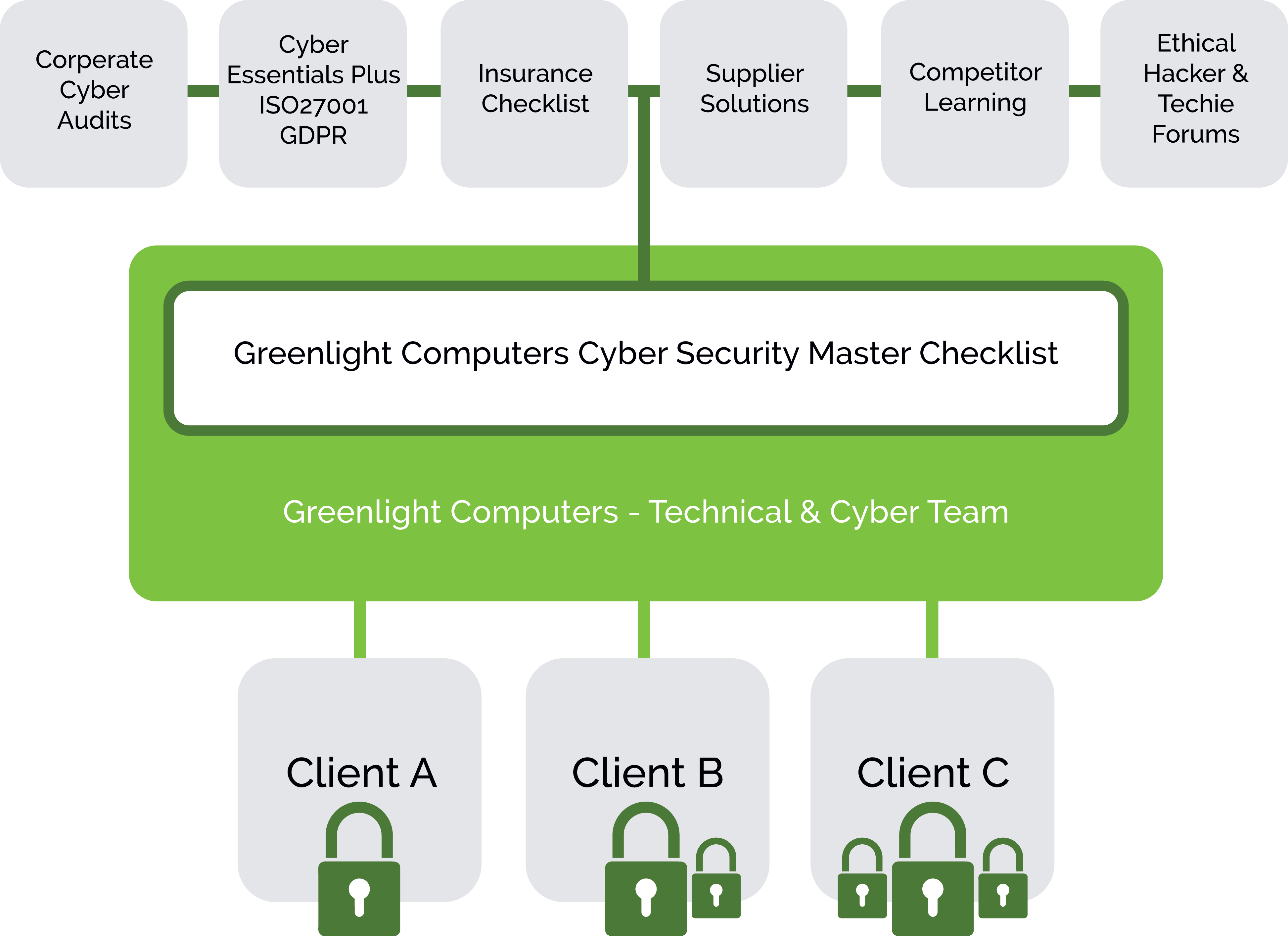
The Greenlight Computers Cyber Security Master Checklist is now a dynamic tool we use daily with clients to review their Cyber Protections and help identify and mitigate risks.
We have listed below a top 20 of basic checks that all businesses should comply with. This is a small subset of our Master Checklist but should provide a useful aide memoire when discussing your Cyber Safety with colleagues.
Following these guidelines will enable you to say YES to a good proportion of any client audit.
To dig deeper please feel free to contact us and we can discuss the more detail requirements your business may have.
Our Top 20 Cyber Protection priorities
1. Anti-virus everything (Servers/Laptops/MAC’s/Tablets/Phones etc)
2. Backup everything
3. MFA (Multi-Factor Authentication) everything
4. Firewall your network
5. Work with an external partner who can bring a wider knowledge base of experience
6. Focus on your Risk Register
7. Segregate your data
8. Standardise where possible
9. Restrict user control where possible
10. Spot check and adapt regularly
11. Have a plan for the worst-case scenario
12. Take Cyber Insurance
13. End of Life replacement
14. Encrypt laptops
15. Secure your website and hosting
16. Server patching maintained, keep software secure and up to date
17. Secure WIFI SSID’s – keep guests and staff segregated
18. Cyber Agents deployed to validate users are maintaining and patching their devices
19. Secure VPN controlling remote access
20. Provide users training and policies to comply with
You can never be 100% safe but with user diligence & cyber protections you can get close.

Item 15 – Website Security
Using WordPress websites as an example, we see many SME’s ensuring their website has a valid SSL certificate HTTPS and assuming that’s security done!! This is not the case. WordPress an excellent open-source CMS used by over 40% of businesses and is designed to provide a flexible methodology for creating professional websites, but this flexibility comes with vulnerabilities that need to be understood and mitigated.
This article from Hubspot provides an excellent summary of potential concerns and how to mitigate them.
• Unauthorized Logins
• Outdated Core Software
• Undefined User Roles
• Outdated Themes and Plugins
• Malware
• Structured Query Language (SQL) Injections
• Search Engine Optimization (SEO) Spam
• Cross-Site Scripting
• Denial-of-Service Attacks
• Phishing
• Supply Chain Attacks
• Hotlinking
• Cross-site Request Forgery (CSRF)
https://blog.hubspot.com/website/wordpress-security-issues
All other technologies have cyber security challenges, similar to those for WordPress users. The advantage for WordPress is that the developer community is huge and share openly their concerns and mitigations, a practice not common with other platforms.

IT Risk Register Template (IT/Cyber Security/GDPR/HIPAA)
Many versions of risk register templates exist but Greenlight Computers recommendation is to keep it simple to ensure senior management reads and comprehends easily.
IT, Cyber Security, GDPR & HIPPA Risk Register
| Open Date | Risk Description | Potential Impact | 3-High, 3-Low Priority | Mitigation | Owner | Status | Close Date |
|---|---|---|---|---|---|---|---|
| 01/02/2022 | LCN email system does not enable MFA | Risk of cyber attack if device acessed | 1 | Move to Microsoft365 and impliment MFA with additional email defender in Bus Premium | Greenlight | Open | 11/02/2022 |
| 01/02/2022 | Endpoint Anti-virus not standard on devices | No ability to centrally monitor | 3 | Look at standardising to ESET End Point to enable central tracking | Greenlight | Open | 11/02/2022 |
Regular review with your IT partner is essential and should be open to both parties creating entries. Typically, the IT partner will identify areas of risk more regularly than internal staff so its imperative that an open relationship exists. Every cyber security incident will present both disruption and cost to client, IT partner and Insurance provider.
Our consultants can help educate your team on running an IT Risk Register as a positive method of maintaining and planning your IT budget.
Cyber Security useful links and good practice
The Greenlight Computers technical and cyber team have come across many sensible articles, videos, statutory pages etc over the years and below are just a few we would recommend should you need to build your knowledge in Cyber Security and Cyber Safety.
We have also established a website www.greenlightcyber.co.uk that starts to identify the ways we can help with your Cyber journey.
Links
This is the Google phishing awareness
https://www.youtube.com/watch?v=R12_y2BhKbE
This is one of a series from National cyber centre
https://www.youtube.com/watch?v=FRxrHduwPjY
GDPR official information from ICO
https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/
Cyber Essentials plus
https://www.ncsc.gov.uk/cyberessentials/overview
Number 1 Tip
Start and maintain an IT Risk Register, together with your outsourced IT partner. It is always better to recognise risk and mitigate where you can, rather than be hit by the inevitable nasty surprises.
This process will also help you budget effectively, and a quarterly or minimum annual review of cyber security is a wise investment for any business.
Contact Us for a more in-depth conversation.
Greenlight offers security assessment and testing services to help clients understand and mitigate against cyber security risks. We work with some of the largest players in the industry to help you protect your business to an appropriate level. No business is 100% secure, the key is to get the protection versus cost balance in your favour and maintain it ongoing.

